Click to zoom in
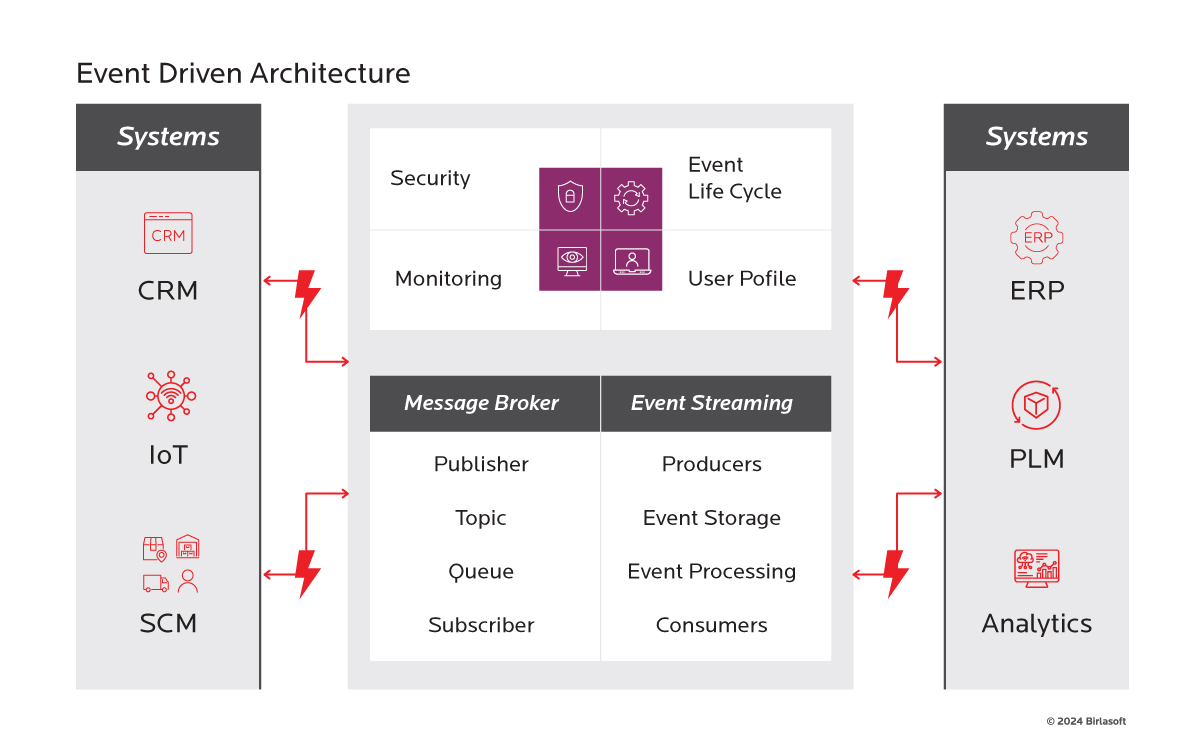
Types of EDA middleware
- Message broker: It is used to ensure reliable event delivery between producers and consumers. It leverages event queues and delivers events to a single consumer. Events can be made to persist to promise at-least once delivery. A limitation of message brokers is a compromise of throughput when consuming services are disrupted.
- Event streams: These are typically used to support real-time data ingestion and processing – for instance, when time-series data is involved. Event streams are usually created in Pub/Sub patterns, where multiple subscribers can consume event streams. While event streams may result in increased latency, they enable high throughput and therefore, work well with large data volumes.
Stay Ahead
Visit our Digital Transformation page
Key characteristics and advantages of event-driven architecture
Event-driven architecture is characterized by the following attributes:
- Asynchronous: In EDA, events are processed independently, as event producers don’t wait for consumers to finish processing.
- Decoupled: Components of EDA are able to scale independently, which reduces dependencies and bottlenecks.
- Replayable: Events can be stored as immutable logs in EDA, which promises high integrity and auditability in mission-critical systems.
- Context awareness: Systems built on EDA can handle events in a context-aware fashion by treating events of different types, origins, and metadata with different logic.
Benefits of adopting event-driven architecture
These characteristics are highly beneficial in high-complexity systems which make use of different infrastructure components and prefer modular components over monolithic ones. Here are some of the key benefits of adopting EDA:
- EDA enables enterprises to efficiently build massive, distributed real-time systems with a massive user base or event density.
- In an EDA-based system, various components can scale independently and dynamically, thus aligning with the requirements of modern computing solutions and infrastructure.
- Software systems based on EDA are highly fault-tolerant as events can be made to persist, and their acknowledgment can be guaranteed by some EDA patterns.
- Optimal EDA-based solutions are cost-efficient as resources are utilized only when an event occurs and triggers downstream processes, making it highly suitable for cloud-based infrastructure.
- Lastly, EDA can improve the responsiveness of systems as various components of it react to events in real-time, while other services continue to function independently.
Key event-driven architecture patterns and their use cases
#1. Event notification
This pattern is used when a service needs to notify another component about the change in a particular state. However, the data or the context related to the event is not delivered to the consumer.
Use cases: used in scenarios where the occurrence of the event needs to be conveyed rather than its specifics – for instance, conveying user likes on social platforms.
#2. Publish / Subscribe
It is also called the Pub/Sub pattern, and the publishers and subscribers are decoupled in this paradigm. In this pattern, more than one subscriber can act on the same event simultaneously.
Use cases: applied when multiple services must respond to an event – for instance, inventory, shipping, and CRM responding to an order placement event.
#3. Event mesh
In this pattern, events are dynamically routed across applications, systems, or locations. Irrespective of the location of services in a network, the event mesh promises accurate delivery of events.
Use cases: typically applied in hybrid implementation patterns that span multiple geographies and complex network topologies.
EDA implementation options
EDA can be implemented on cloud, on-premises, and in hybrid scenarios where some components are in the cloud and others are located on premises. Take a look at these scenarios below:
- EDA on cloud: The key benefit of implementing EDA on cloud, is that the services offered by cloud providers abstract all the operational overheads away from you. All cloud providers offer dedicated services for message broking (AWS SQS, SNS, Azure Service Bus, Google Cloud Pub/Sub) and event streaming (AWS Kinesis, Azure Event Hubs, Google Cloud Dataflow) and typically offer autoscaling and optimized resource utilization.
- EDA on-premises: This may be required in cases where sensitive data is involved, which cannot be stored or processed in the cloud. While implementing EDA on-premises enables compliance, the onus of handling software, hardware, and network operations falls onto you. When implemented on-prem, platforms like RabbitMQ, Kafka, and Solace are used.
- Hybrid EDA implementation: Such implementations work well with the event mesh pattern, although other EDA patterns can also be adopted. It typically requires hybrid integration platforms like Azure Integration Services or MuleSoft to bridge cloud and on-prem environments. Hybrid EDA implementations are best used when data can be maintained on-prem, but the cloud can be leveraged to process it confidentially and securely.
Best practices when applying event-driven architecture
The benefits and upsides of EDA can quickly turn into unmanageable complexity if the architecture definition is suboptimal. Here are a few best practices that you can adhere to, and avoid such pitfalls:
- Clear event definitions: Standardize event schemas and semantics to ensure seamless communication across all components.
- Loose coupling: Keep producers and consumers independent to enable flexible system evolution and easier scalability.
- Idempotent event processing: Ensure event handlers can safely process repeated events without causing issues or inconsistencies.
- Centralized monitoring: Implement robust logging and observability to easily track, debug, and monitor event flows.
- Scalable architecture: Build systems that can efficiently handle fluctuating event volumes while maintaining performance.
- Ensure data consistency: Apply strict integrity checks during event processing to guarantee accurate and reliable data handling.
- Secure event transmission: Protect event data with encryption and integrate compliance checks to prevent unauthorized access and breaches.